Privacy Dimensions and Issues in Online Social Networks
The ubiquity of information communication technologies which is leading to present-day digital society has changed the basic principles of human interaction. Although, privacy, as a one of these principles, has been noted from several decades ago, it is attracted a lot of attention during the recent years. Online social networks (OSNs) (e.g., Facebook, LinkedIn, MySpace), as a particular type of virtual community, attempt to provide helpful functionalities including maintaining/increasing social relationship, finding users with similar interests, improving our knowledge, and financial benefits, the published data in such environments can violate various aspects of users’ privacy. In fact, users are virtually interacting continuously, and disclose various levels of private information of themselves or others unconsciously. Therefore, OSNs are one of main bridges of revealing personal information by allowing users to upload their footprints (e.g., text, images, and videos) and interact with others in a variety of ways. Moreover, by raising the number of users of an OSN which lead to more dissemination of information, as well as sharing different varieties of information within many OSNs, users’ privacy concerns may increase. In the following, some challenging problems which users and OSN providers are facing due to preserving privacy of users have been discussed.
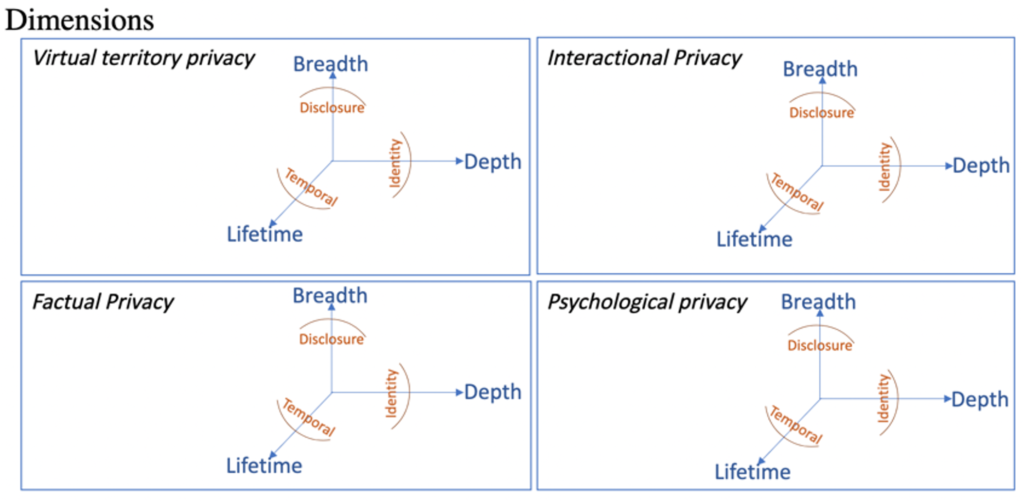
First, privacy is a multi-dimensional concept specially when it is under investigation in OSNs context. Usually, four-dimensional privacy concept, explained in the following, including virtual territory privacy, factual Privacy, interactional Privacy, and psychological privacy has been discussed. Virtual territory privacy: differing from physical privacy which is defined as the freedom from surveillance and unwanted intrusions upon one’s space by the physical presence, touch, sights, sounds, or odors of others, in the virtual social context, there are no physical boundaries that help define the private territory. However, people still feel ownership of the digital belongings that they are entitled to or that are created by them (for example, web-logs, personal spaces, profile pages, etc.). Factual privacy: refers to ability to control identifiable personal information about oneself. Interactional privacy: individuals may feel compelled by or uncomfortable under some circumstances relating to social interaction. For example, conversation requests may be initiated obtrusively or at inappropriate times. Psychological privacy: people need the freedom to express their own views and the capability to hide themselves from norm that they do not agree with. Psychological privacy protects the individual from intrusions upon one’s thoughts, feelings, and values.
Second, each user usually has a scope in his/her mind before publishing any data on OSNs, and privacy requires keeping the published information in its predesignate scope. This scope is defined by breadth (the distribution of audience), depth (the degree of allowed usage), and lifetime (the long life of the published data). When a piece of information is moved beyond its predesignate scope in any of these dimensions (accidentally or maliciously), a privacy breach occurs. Therefore, a breach may occur when information is shared with a party for whom it was not intended (disclosure), when information is abused for a different purpose than was intended, or when information is accessed after its intended lifetime. Aside from the scope, users in OSNs are contending with privacy three boundaries including disclosure (users try to handle the anxiety of disclosing their information in a public or private manner), identity (The identity boundary is described as the ability to manage one’s information with particular groups. For example, it shows users’ behaviors in different situations: one at work and the other at a party), temporal (It shows how the conduct of individuals may differ over time).
Privacy has various dimensions, and users try to consider different scopes and have different boundaries. Our notion in relation between the dimensions, scopes, and boundaries has been presented in Fig1. Each dimension has its corresponding scopes, and each user has a different boundary for each scope.
Finally, to perfectly utilize the provided functionalities of an OSN, users need to publish more information, thus, there is a tradeoff between optimal use of functionalities and user privacy. Moreover, another issue called privacy paradox (see this blog for further information) has been observed in users’ online behavior. Recent research has revealed discrepancies between user attitude and their actual behavior. More specifically, while users claim to be very concerned about their privacy, they nevertheless undertake very little to protect their personal data.
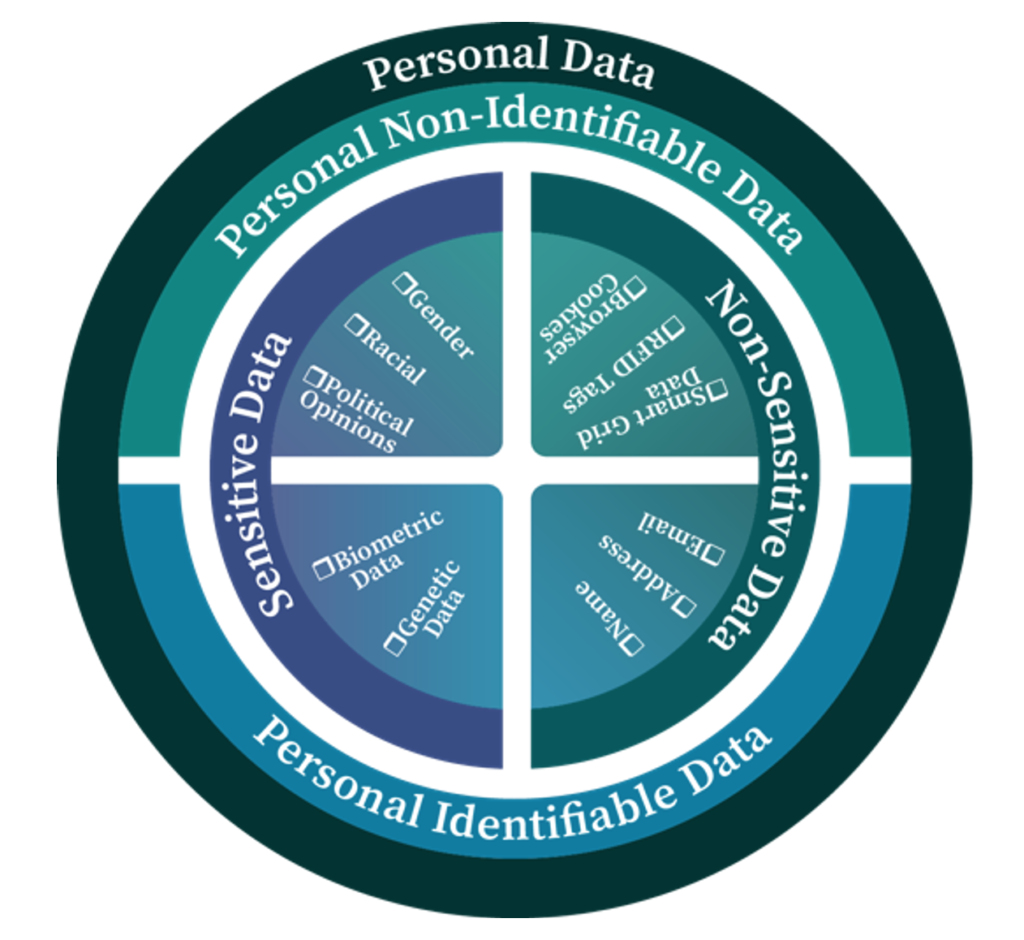
Notably, personal data can be categorized as personal sensitive/non-sensitive or identifiable/non-identifiable data (Fig. 2). Personal identifiable data can be directly linked to a specific individual such as social security number, e-mail, driver’s license number, usernames, biometric data. Personal non-identifiable data does not include any personal references, and thus, does not fall under the material scope of the GDPR. Sensors that collect data for applications, e.g. made for climate analysis or the monitoring of industrial complexes do not process personal data at any stage. Based on article 9 of GDPR, personal data consisting of the following categories of data is considered as personal sensitive data: a) racial or ethnic origin, b) political opinions, c) religious or philosophical beliefs, d) trade union membership, e) data concerning health or sex life and sexual orientation, f) genetic data, g) biometric data where processed to uniquely identify a person. Among the above 7 categories, categories f and g can be considered as personal identifiable data, and the rest as personal non-identifiable data by itself.
Conclusion
Considering all dimensions of privacy and users’ scopes to preserve the privacy of users in OSNs is extremely challenging. As a solution, OSNs provide policies and privacy settings to control and adjust who can access users’ profiles and posts. However, privacy polices offered by the system are confusing and expressed in legal jargon that is difficult to understand. Furthermore, privacy settings are complex, time-consuming, and still insufficient to fully protect users’ privacy. Besides, OSNs providers mostly store, process and analyze users’ data and sometimes sell them to third-parties for advertising and marketing purposes. Although, to prevent privacy breaches in OSNs, privacy has been investigated from various perspectives (i.e., social, legal, and technical) among researchers. For instance, regarding technological issues, since smart phones are now fully powered to connect OSNs, privacy threats categorically related to cell phones should be considered as a main bridge of disclosing sensitive information. Threats and vulnerabilities (see this blog for further information) in mobile social network applications and gadgets already installed in mobile devices may cause more privacy issues.
This blogpost was written by Ahmad Hassanpour. As an AI engineer, he worked on various projects such as face recognition system, object detector, fire detector, intelligent EEG and ECG signal analyzer, video classifier, etc.