A Discussion on Privacy Design and Consent from Mobile Sensor Permissions
Introduction
Nowadays, the pervasiveness of mobile devices is contributing to the rapid digitalization of society, and it is making room for unprecedented Human-Computer Interaction (HCI) scenarios. People spend a large share of their time using their devices for several purposes, including communication, entertainment, internet browsing, orientation, education, banking, tracking physical activity, etc.
Certainly, the usefulness of mobile devices is also due to the number of sensors they usually come equipped with. Several physical quantities are routinely measured for different purposes and applications since most devices have powerful computing capabilities and are constantly connected to the internet. On the flipside, it has been shown that such measurements offer a very accurate description of an individual, including traits that are considered sensitive by the GDPR, such as demographic information, activity and behavior, health parameters and body features, mood and emotion, location tracking, and typed text inference. The scientific literature is full of examples of inference of one or more of these characteristics from mobile sensor data, collected in a transparent way, in other words, without having the user perform any specific action, nor noticing. A survey of the information extracted by such data is available in [1].
Apart from cameras and microphone, which, despite being a major source of user biometric data, have specific permissions, this post will be focused on other traits less protected in terms of privacy. After analyzing what are the biometric traits captured by mobile devices, and the possibilities typically offered by operative systems to the users to protect their privacy, a discussion of the concept of design of privacy and consent will be carried out.

Mobile Sensors
In general terms, the sources of information on mobile devices are represented by: (i) hardware sensors, physically installed components that perform a transduction of the physical quantity they measure into an electrical signal, which is converted into the digital domain for further processing; (2) software sensors, that rely on data already made available by hardware sensors and/or calculate them to produce a measurement.
All sources of information can be divided into five broad categories:
– Motion sensors are responsible for measuring the acceleration and rotational forces in the three axes of the device. Hardware-based motion sensors will register continuous quantities as in the case of acceleration or angular velocity, whereas, when software based, their output could be either continuous or event driven, as in the case of a step detector. These sensors are typically used for improving the user experience (as in the case of rotating the screen, smart unlock, gaming, navigation), or for fitness purposes.
– Position sensors span from Earth’s magnetic field sensors for orientation in space to proximity sensors. The application purpose of position sensors is similar to motion sensors, including features to optimize the user experience such as in the case of augmented reality applications, or simply the microphone activation and screen deactivation during calls.
– Environmental sensors generally measure scalar quantities such as the light intensity, pressure, temperature, humidity. For instance, they are useful to automatically adjust the screen brightness, or to provide contextual information.
– Numerous physiological and biological parameters are made available thanks to dedicated health sensors. For example, most smartwatches include built-in optical sensors to capture changes in blood volume in the arteries under the skin, from which heart-related and sleep quality measurements can be obtained. Most of these are designed for the users who are interested in monitoring their physical activity.
– Touchscreen data can be in the form of keystrokes acquired from the keyboard or in the form of touch data acquired throughout the user interaction. In the former case, the virtual keys pressed are logged together with pressure and timestamps for each key press and release. In addition, it is possible to track the position of the fingers on the touchscreen in terms of X and Y coordinates, velocity, acceleration, angle, and trajectory of the pressed points, as well as finger size pressure information. Such information can be used for behavioral biometric user authentication, and to improve usability as in the case of the different touch gestures (tap, pinch, zoom, scroll, etc.) available.
Sensor Permissions in Android
In this post we will consider Android as its share covers over 70% of the total smartphone operative system market (2022). In the phone settings, users can typically exercise their right to privacy in the dedicated “Privacy” section. A Permission Manager tool is typically available to quickly check what permissions have been granted to any of the installed apps, and to manage them according to the user’s preference.
As it is possible to see in the image on the left, all permissions are grouped into 13 categories. The several and diverse sensors described in the previous section are all included in only 2 of the categories presented. The description available on the Android documentation is reported below:
– Body sensors: Allows an application to access data from sensors that the user uses to measure what is happening inside their body, such as heart rate.
– Physical activity: Allows an application to recognize physical activity.
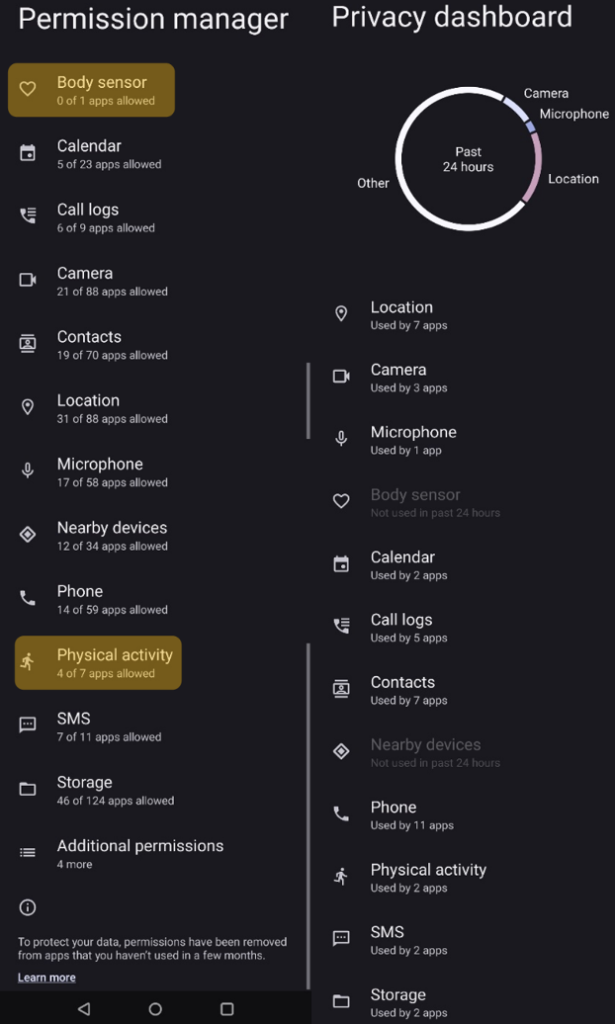
In addition, a Privacy Dashboard is also available to monitor what data have been used by which application, to spot unnecessary and possibly malicious user data usage.
Therefore, several independent sources of information are all regulated, in terms of privacy, by only two permissions with a short description. Moreover, there is no specific permission about touchscreen data, which have also been demonstrated to be a rich ground for inferring user sensitive and personal information.
The Design of Privacy Tools
In this context, the design and engineering of such privacy features seem crucial. On one hand, it is legitimate to ask how users can have control over their privacy if the “privacy knobs” at their disposal have such intrinsic limitations. Some might consequently argue that finer privacy granularity might be needed. On the other hand, it would not be convenient for app developers having to deal with a specific permission for each single one of the installed sensors. Additionally, the final non-technical end users might even feel overwhelmed if the number of permissions is excessive, failing once again in managing privacy virtuously.
In this scenario, it is evident that a compromise must be sought among the parties (end user vs. apps profiting with user data), and that the usage of the collected data should be necessary and proportionate, as promoted by the GDPR [2], which also identifies consent as just one of the six legal bases outlined in Article 6. Consequently, an open question would be whether the currently adopted trade-off design is the optimal one.
The Limitations of Consent
Nevertheless, there is another question which digs deeper into this debate and that it is ultimately more important for users to ponder and to be conscious of. What is the role that consent play in privacy and data protection today? As argued in [3], modern privacy law really came about in the 1960s from an academic point of view, representing the right to privacy as the claim of individual groups or institutions to determine from themselves when, how, and to what extent information about them is communicated to others. Such definition appears as very well formulated: who could be against consent? However, despite the fact that challenging consent would be totally counterintuitive in the world of privacy, because privacy is so closely linked to ourselves, and our autonomy, it is both unpractical and undesirable that we focus on consent. As examined in [3], there are 7 reasons why consent-based approaches to privacy protection are limited. They are:
1) Unpracticality of privacy notices. A study from 2008 calculated that to read the privacy notices of the 45 most popular websites online would take an individual 30 full working days a year. For instance, PayPal’s privacy notices includes 36275 words, while iTunes’ 19972.
2) Impossibility of granting or denying consent, which turns out to be inaccessible (for instance, cameras recording in the street, or specific mobile sensors).
3) Lack of effectiveness, as people ignore privacy notices or consent control tools.
4) Illusory nature of consent, since it is not possible to deny it and still use a device or application.
5) Huge burden on individuals, transforming their privacy in a duty, rather than a right.
6) Consent cannot be absolute, as it can be overruled in some cases (for instance for public security related purposes).
7) Consent leads to poor privacy protection, as agreeing to terms corresponds to renouncing to privacy.
The EU GDPR has shifted the focus of privacy protection law, as it does not require businesses to obtain consent from people before using their personal information for their purposes. Rather, consent is just one of the legal, and businesses must identify the legal basis for their data processing. Moreover, if a business data processing causes harm, they cannot shift liability by asking consent.
Conclusions
In this blog post, a description of the sensors typically installed on mobile devices has been provided, showing the correspondent privacy options available for the user on Android. This case study was adopted to prompt a discussion over the importance of the design of privacy protection control tools, followed by a summary of an interesting examination [3] of the concept of consent in today’s privacy protection scenario. As seen, consent is not central in the GDPR, but from the users’ point of view it still is, considering the number of times businesses require users’ consent for data processing. In any case, the privacy protection debate is not settled yet, and it is hoped that useful ideas were provided in this post to reflect over and consciously live in today’s technological era.
References
[1] P. Delgado-Santos, G. Stragapede, et al. “A Survey of Privacy Vulnerabilities of Mobile Device Sensors”, ACM Computing Surveys (2022),https://dl.acm.org/doi/full/10.1145/3510579
[2] “Necessity & Proportionality”, European Data Protection Supervisor,https://edps.europa.eu/data-protection/our-work/subjects/necessity-proportionality_en
[3] F. Cate, “Data Privacy and Consent” , TEDxIndianaUniversity (2020),https://www.youtube.com/watch?v=2iPDpV8ojHA&ab_channel=TEDxTalks
Image source
This blogpost was written by Giuseppe Stragapede. He received his M.Sc. degree in Electronic Engineering from Politecnico di Bari, Italy, in 2019. After one year as a computer vision engineer in the industry, in 2020 he started his PhD with a Marie Curie Fellowship within the PriMa (Privacy Matters) EU project in the Biometrics and Data Pattern Analytics – BiDA Lab, at the Universidad Autonoma de Madrid, Spain. His research interests include signal processing, machine learning, biometrics and data protection.